A rootkit is a type of software that is designed to gain administrator-level control over a computer system without being detected.
RootRepeal is a new rootkit detector. It is designed with the following goals in mind:
- Easy to use - a user with little to no computer experience should be able to use it.
- Powerful - it should be able to detect all publicly available rootkits.
- Stable - it should work on as many different system configurations as possible, and, in the event of an incompatibility, not crash the host computer.
- Safe - it will not use any rootkit-like techniques (hooking, etc.) to protect itself.
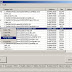
- Driver Scan - scans the system for kernel-mode drivers. Displays all drivers currently loaded, and shows if a driver has been hidden, and whether the driver's file is visible on-disk.
- Files Scan - scans any fixed drive on the system for hidden, locked or falsified* files.
- Processes Scan - scans the system for processes. Displays all processes currently running, and shows if a processes is hidden or locked.
- SSDT Scan - shows whether any of the functions in the System Service Descriptor Table (SSDT) are hooked.
- Stealth Objects Scan - attempts to determine if any rootkits are active by looking for typical symptoms.
- Hidden Services Scan - scans for hidden system services.
- Shadow SSDT Scan - counterpart to the SSDT Scan, but deals mostly with graphics and window-related functions.
Simply run RootRepeal.exe by double-clicking on it. No installation is necessary.
How do I know if I have a rootkit?
Run a system scan using the "Report" tab, and send the log to an expert for analysis.The SSDT is a table that stores addresses of functions that are used by Windows. Whenever a certain type of function is called, Windows looks in this table to find the address for it. However, a lot of rootkits and some legitimate software hooks this table, redirecting these requests. This type of hooking can be used to hide just about anything on Windows.





0 comments:
Post a Comment